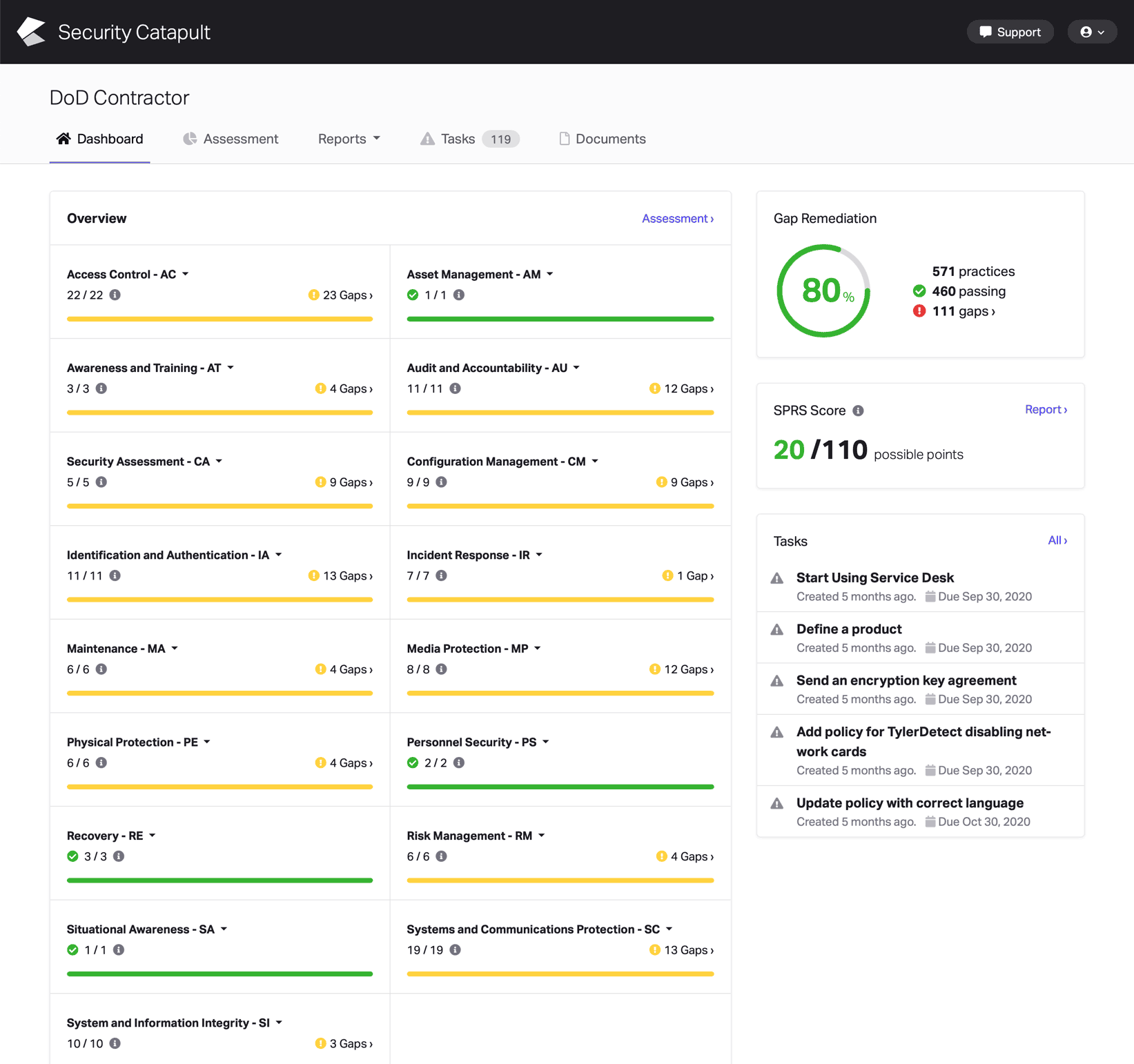
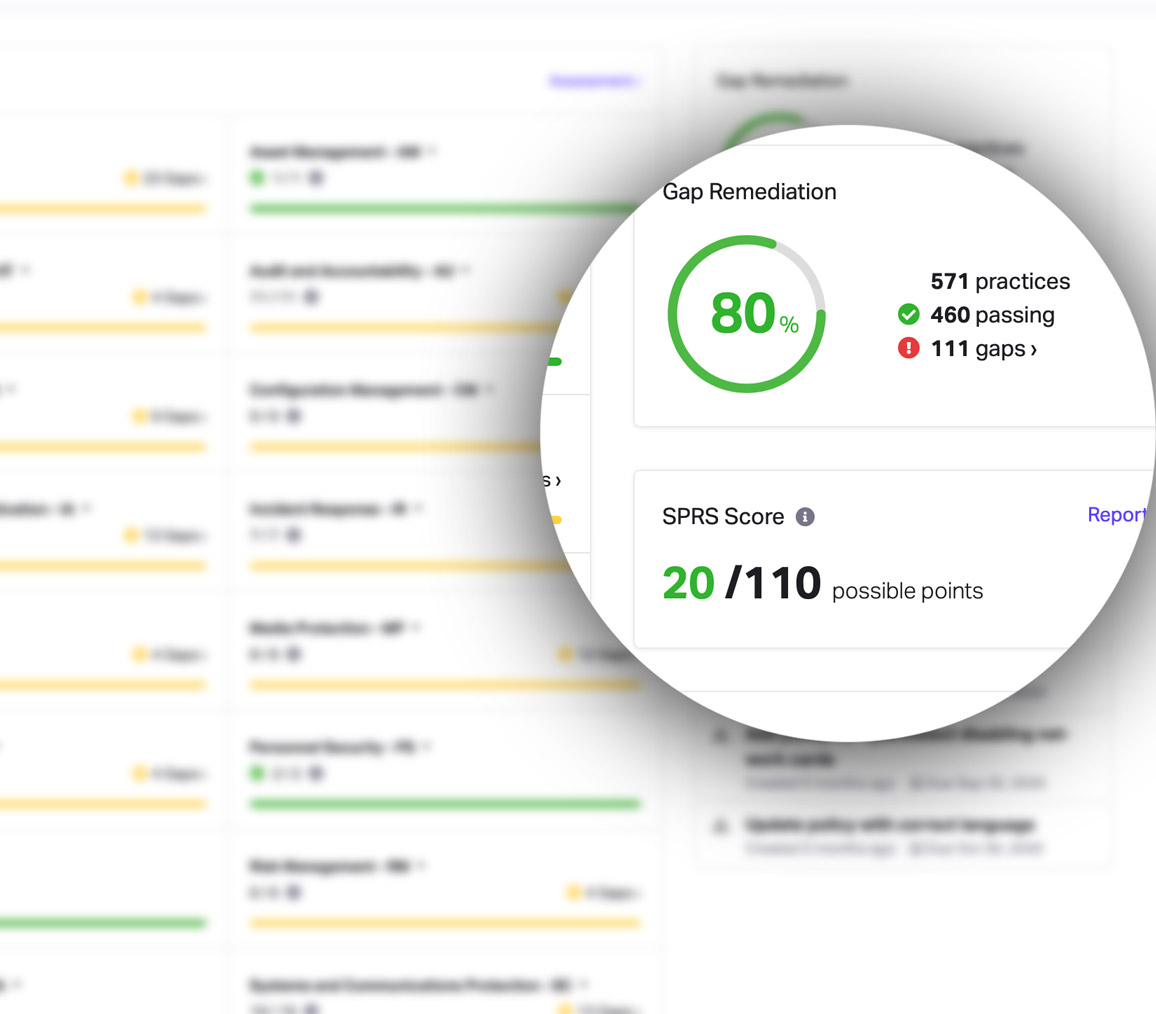
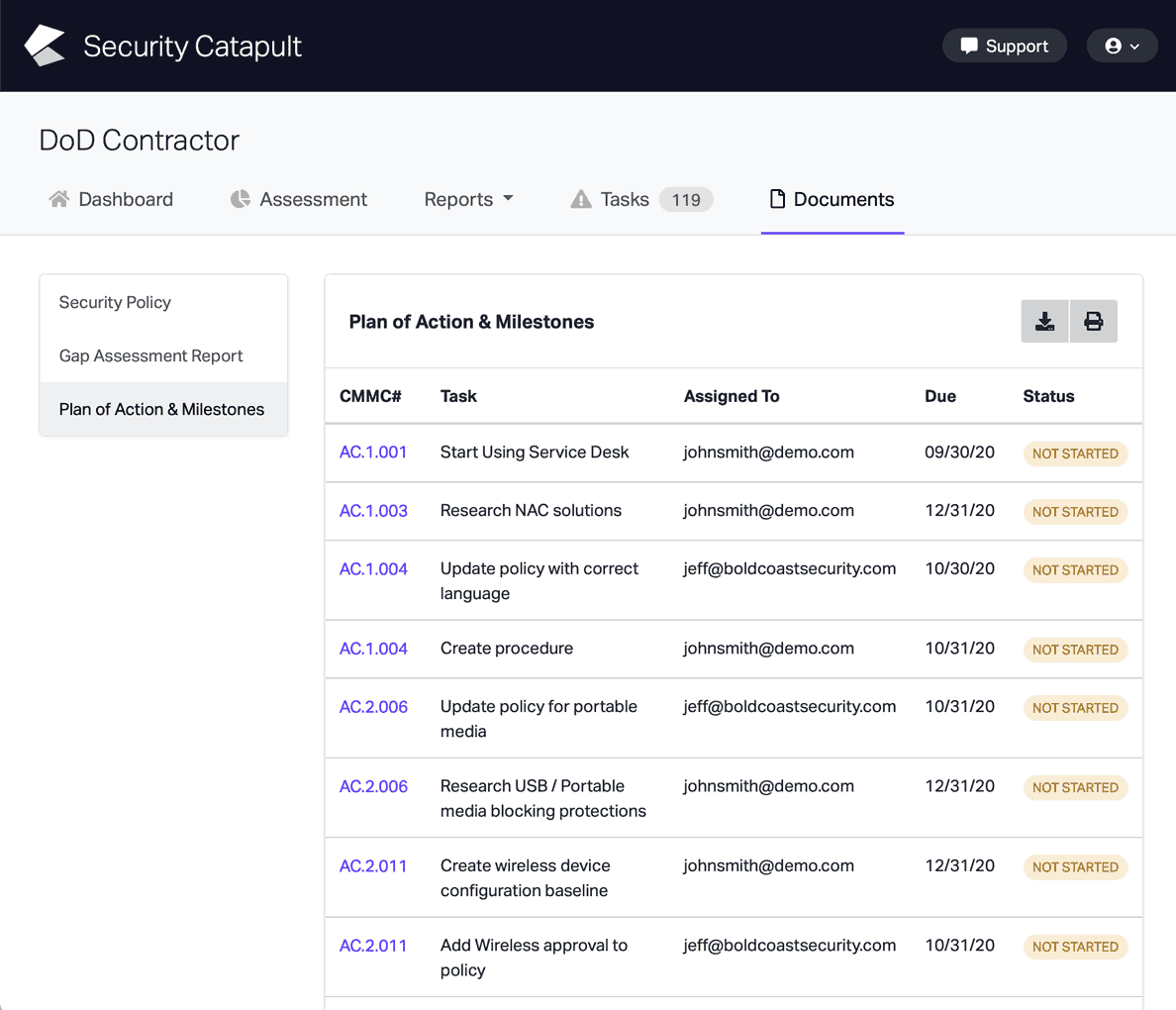
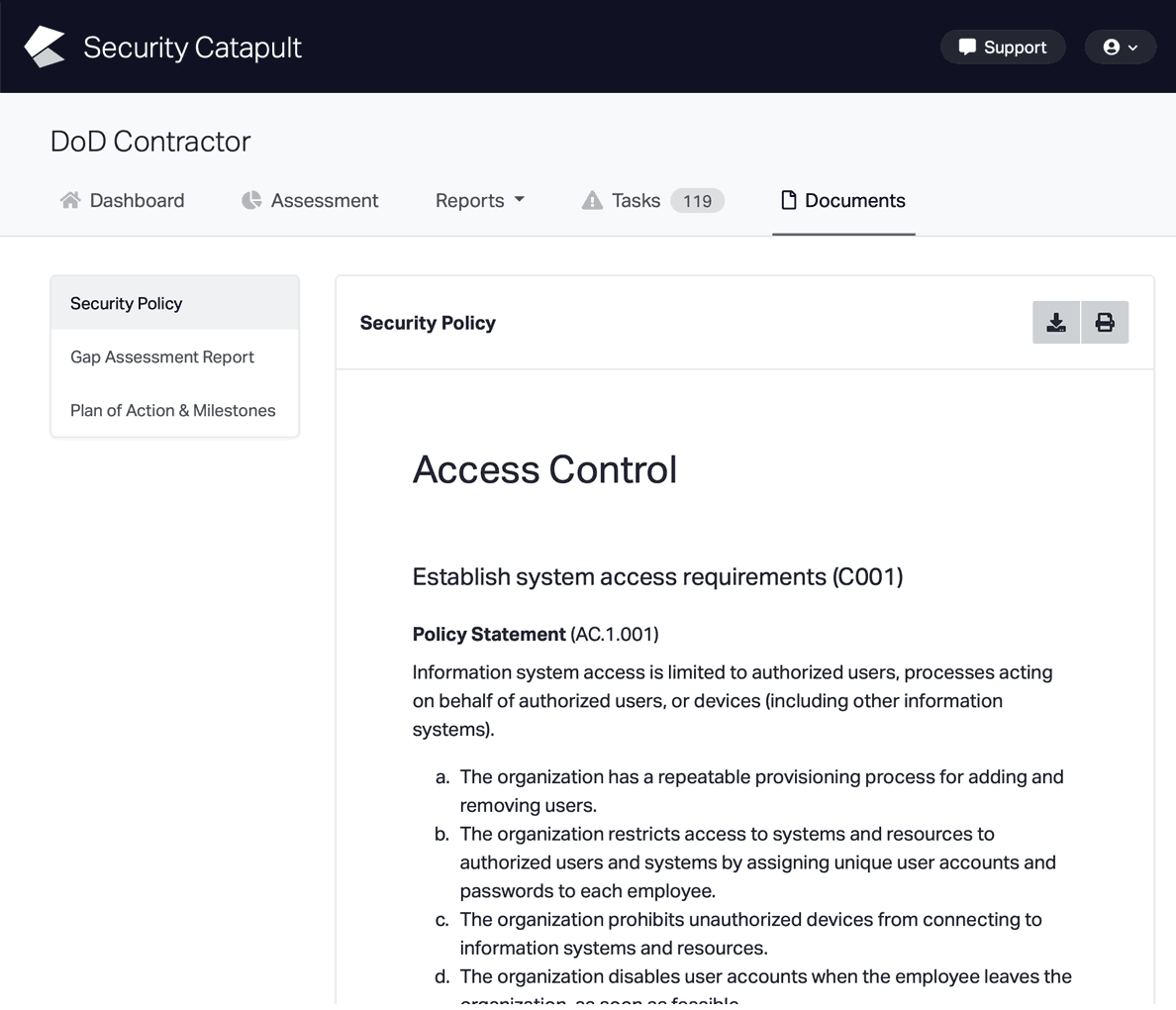
CMMC Practice AC.L1-3.1.1
Authorized Access Control: Limit system access to authorized users, processes acting on behalf of authorized users, and devices (including other systems).
Monarch ISC Guidance
Discussion From Source
References
- FAR Clause 52.204-21 b.1.i
- AU ACSC Essential Eight
- CIS Controls v7.1 1.4, 1.6, 5.1, 14.6, 15.10, 16.8, 16.9, 16.11
- NIST CSF v1.1 PR.AC-1, PR.AC-3, PR.AC-4, PR.AC-6, PR.PT-3, PR.PT-4
- NIST SP 800-53 Rev 4 AC-2, AC-3, AC-17
- CERT RMM v1.2 TM:SG4.SP1
- NIST SP 800-171 Rev 2 3.1.1