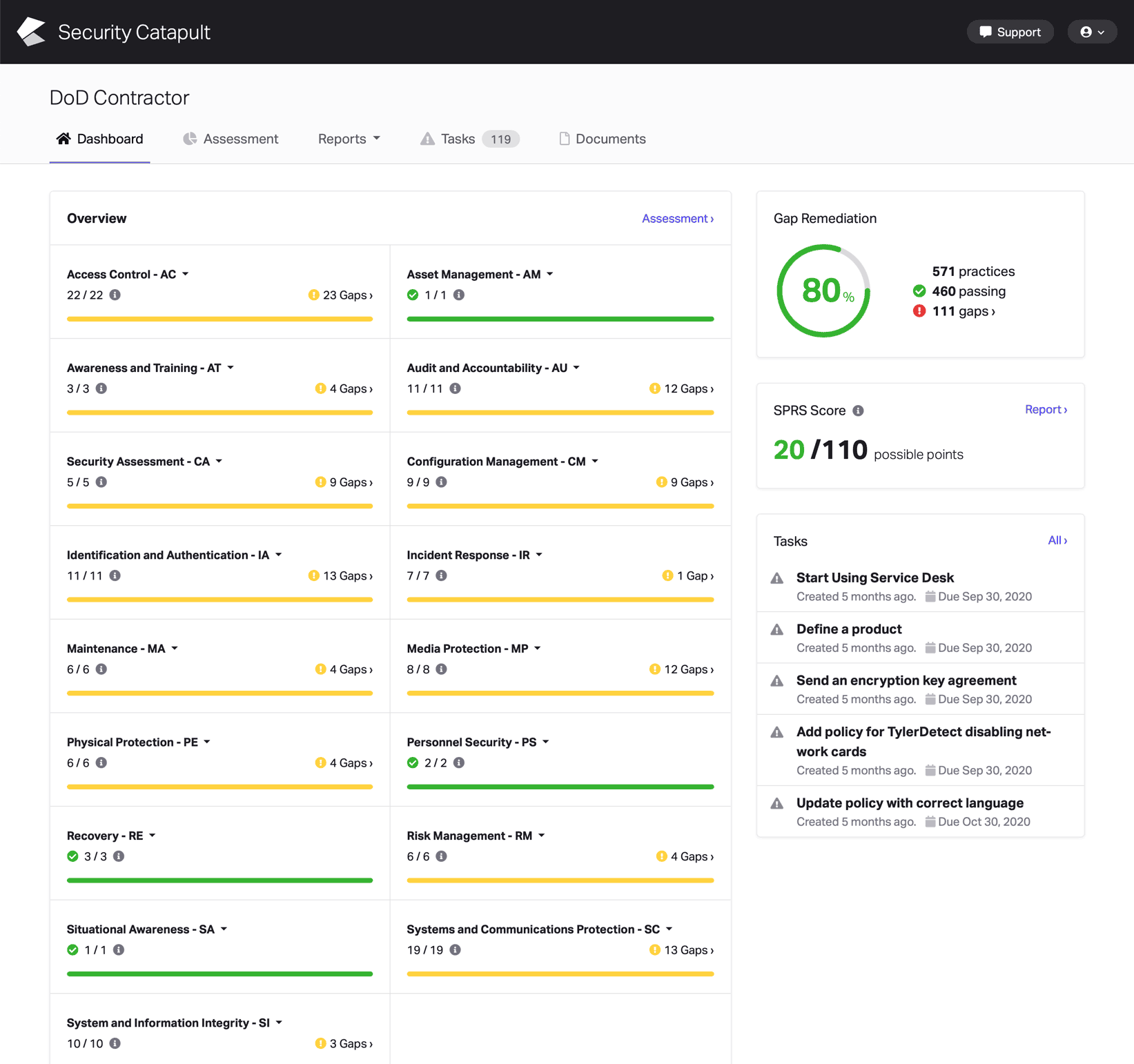
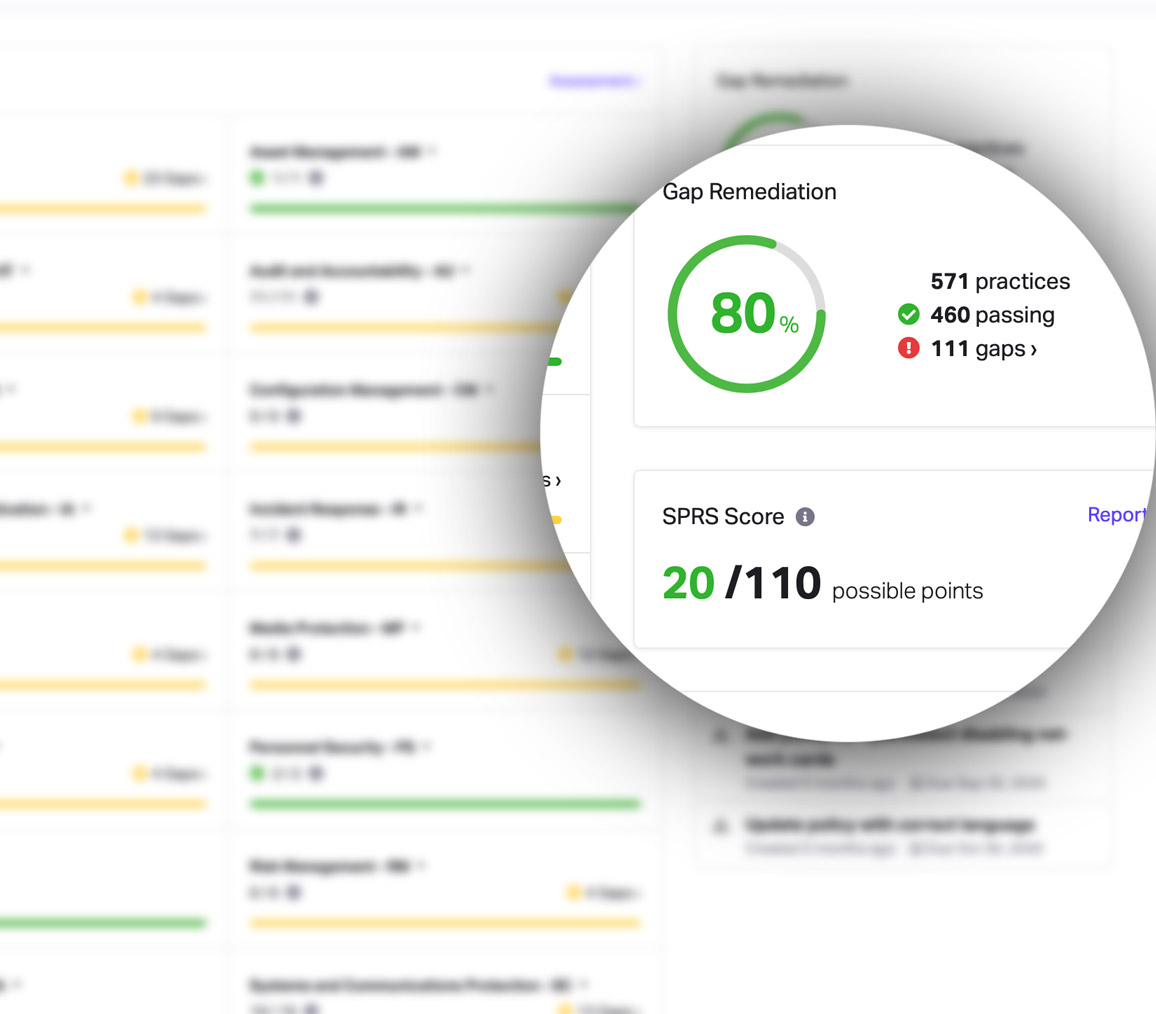
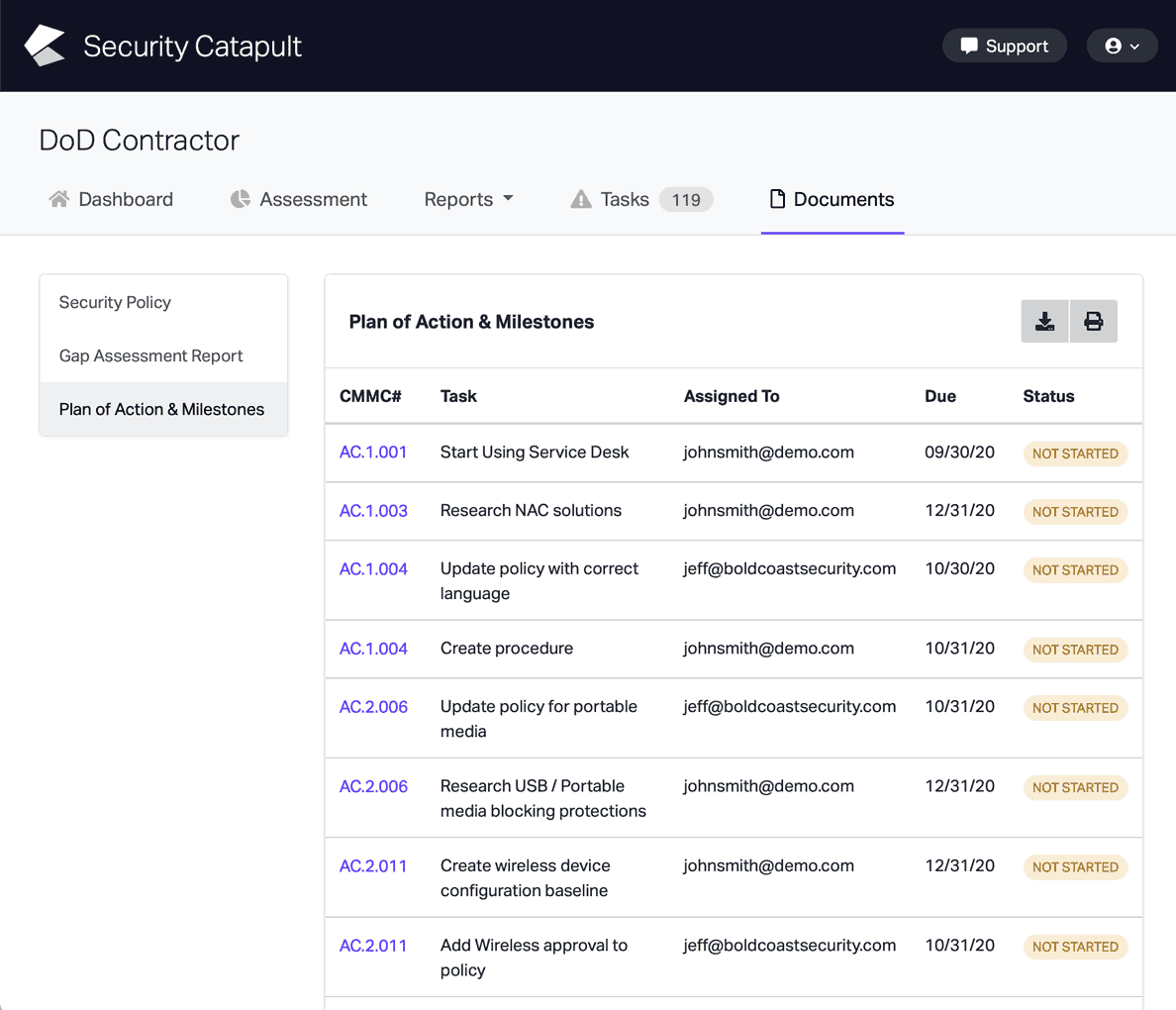
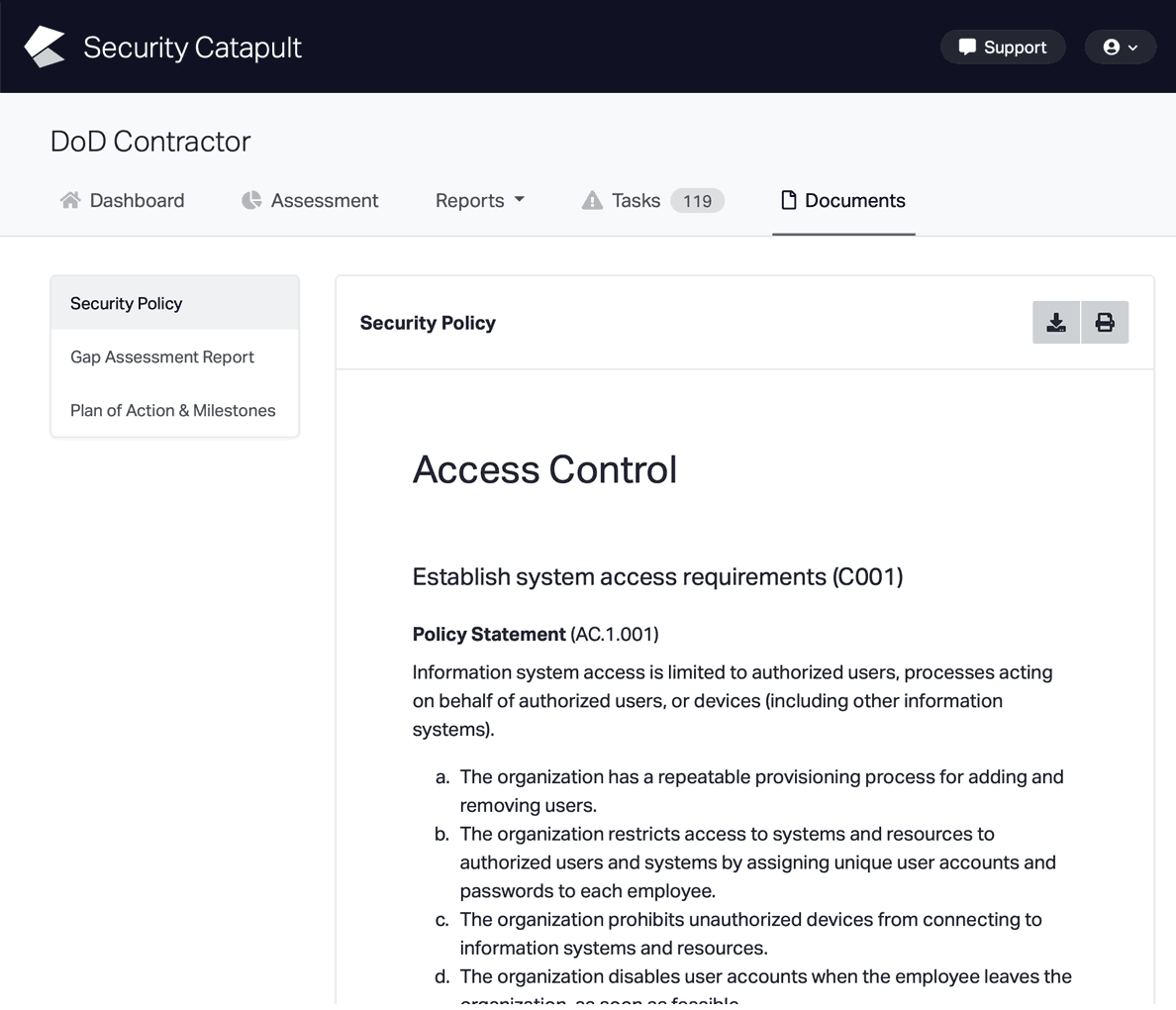
CMMC Practice CA.L2-3.12.4
System Security Plan: Develop, document, and periodically update system security plans that describe system boundaries, system environments of operation, how security requirements are implemented, and the relationships with or connections to other systems. ***Note: According to the DoD Scoring system, failure to comply with this practice by having no System Security Plan is an automatic failure of all practices.***
Monarch ISC Guidance
Discussion From Source
References
- NIST CSF v1.1 PR.IP-7
- NIST SP 800-53 Rev 4 PL-2
- x
- x
- x
- NIST SP 800-171 Rev 2 3.12.4