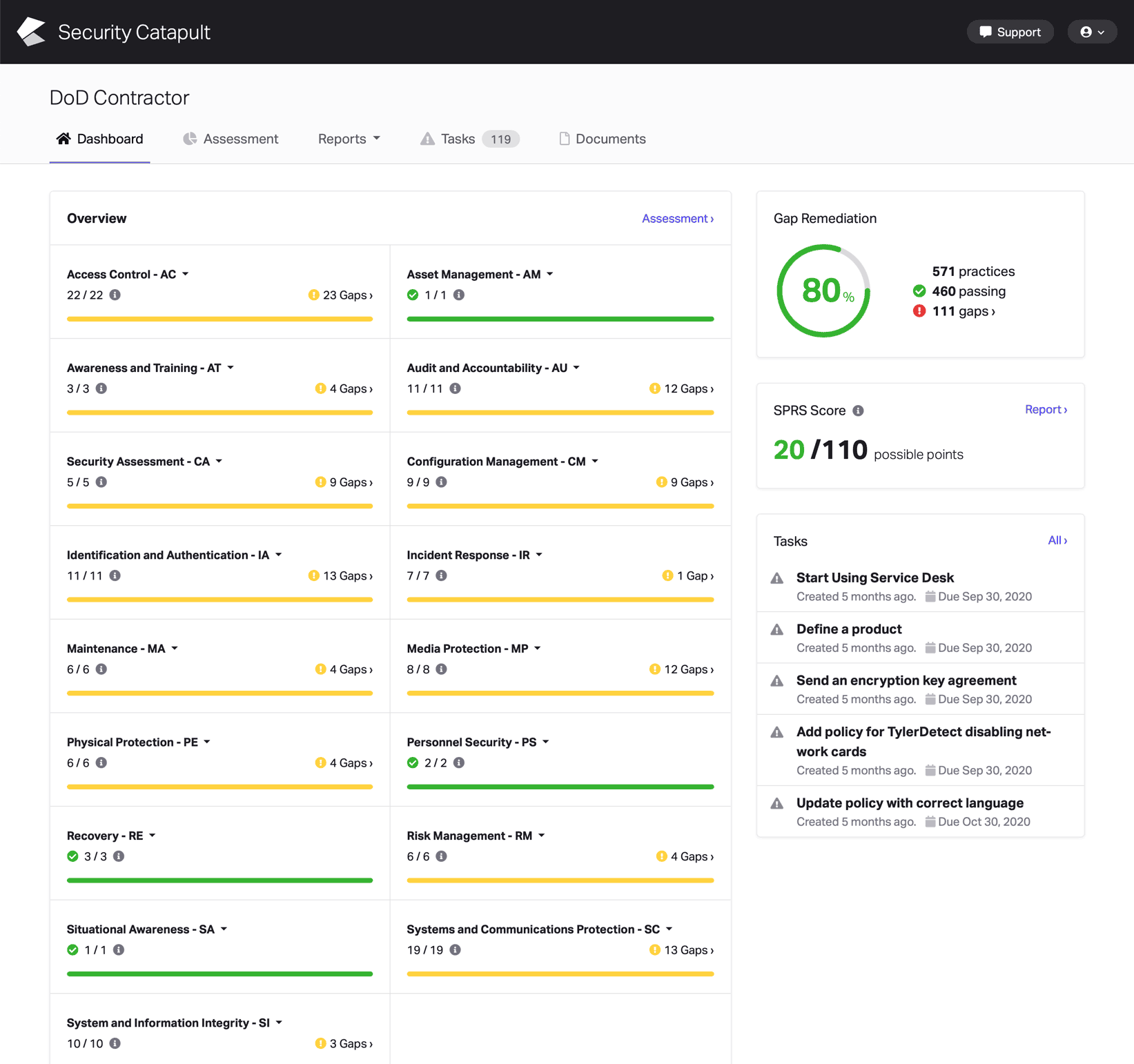
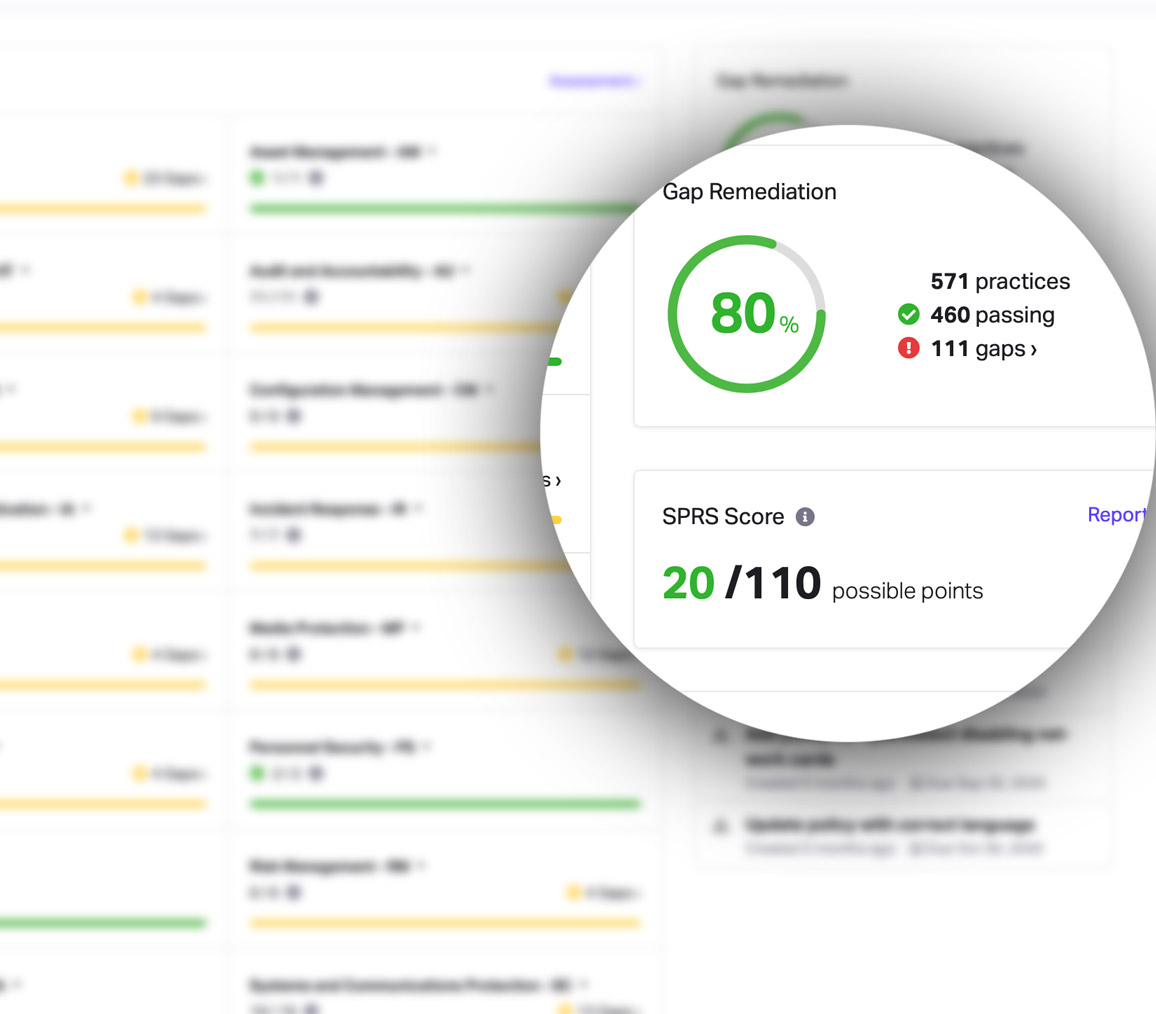
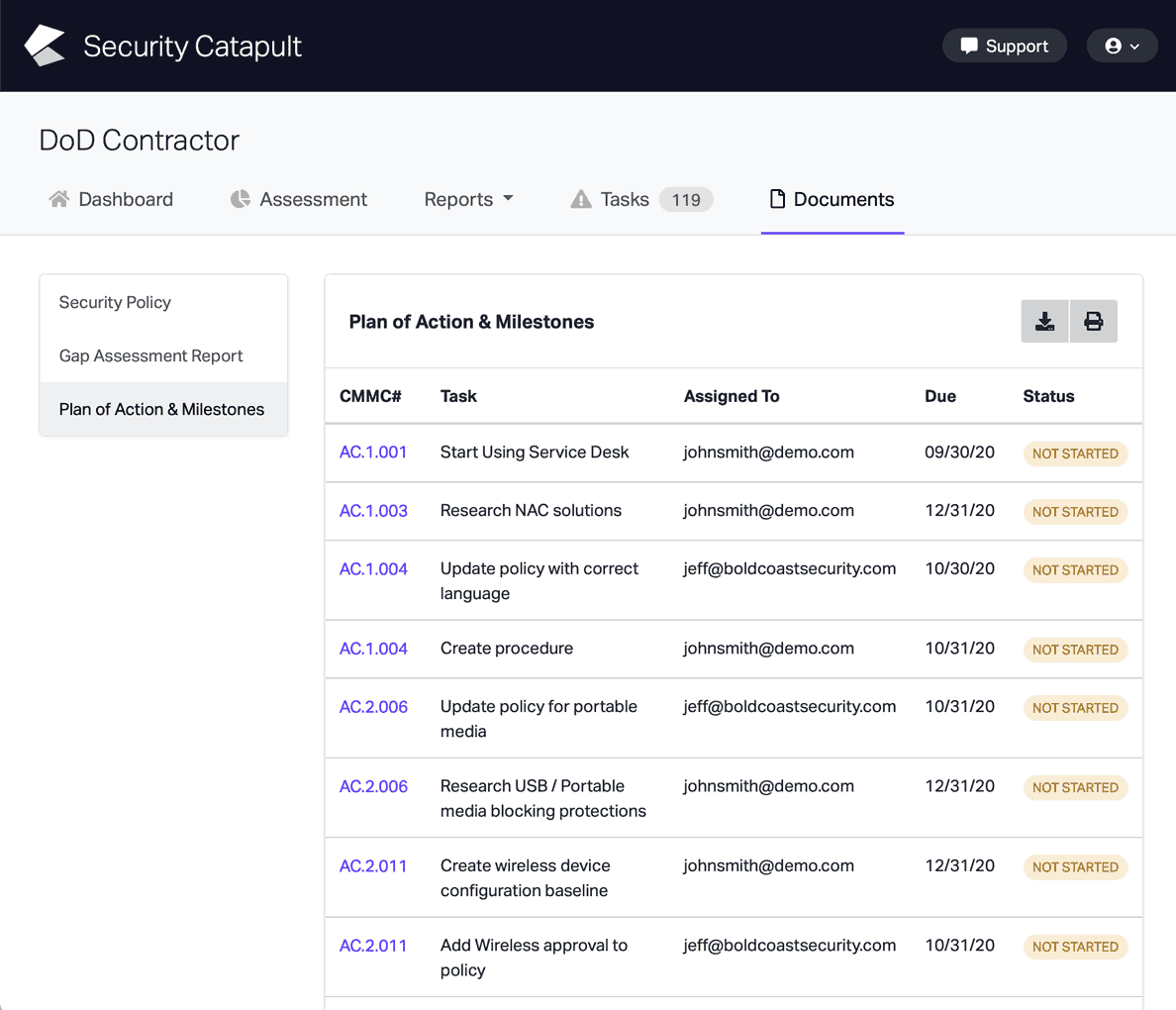
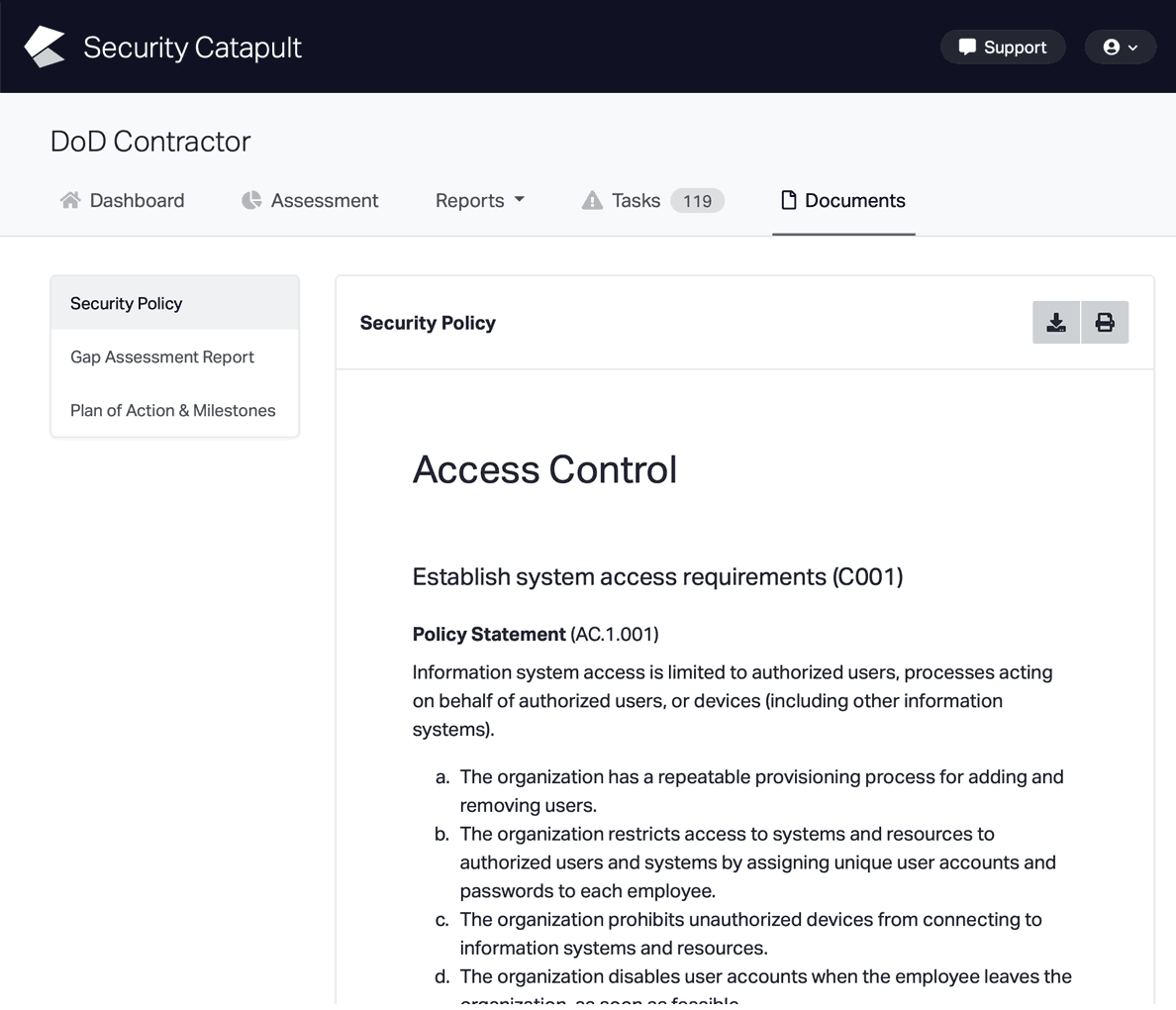
CMMC Practice CM.L2-3.4.3
System Change Management: Track, review, approve, or disapprove, and log changes to organizational systems.
Monarch ISC Guidance
Discussion From Source
References
- AU ACSC Essential Eight
- CERT RMM v1.2 KIM:SG5.SP2
- NIST SP 800-171 Rev 2 3.4.3
- NIST CSF v1.1 PR.IP-1, PR.IP-3
- NIST SP 800-53 Rev 4 CM-3