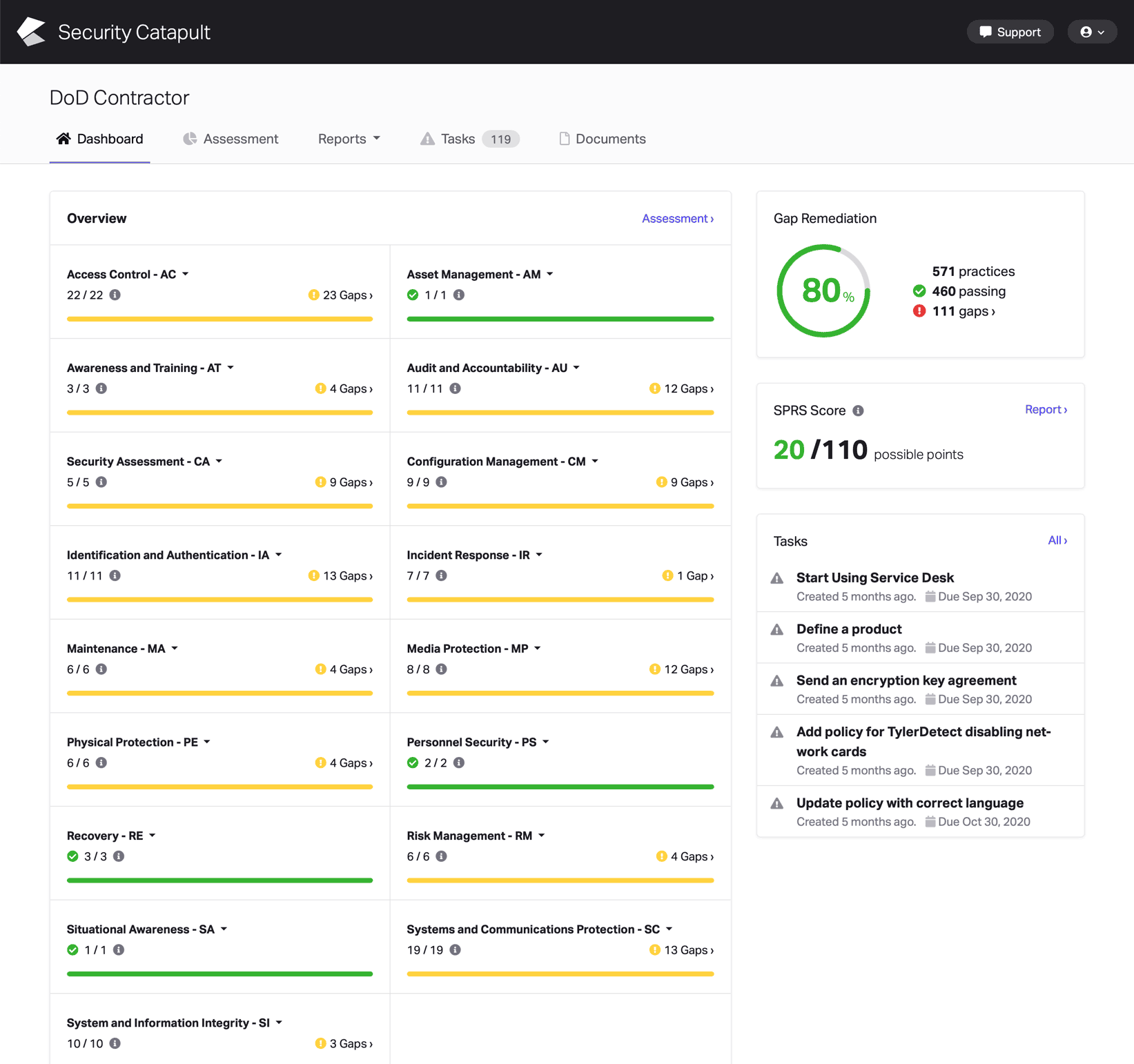
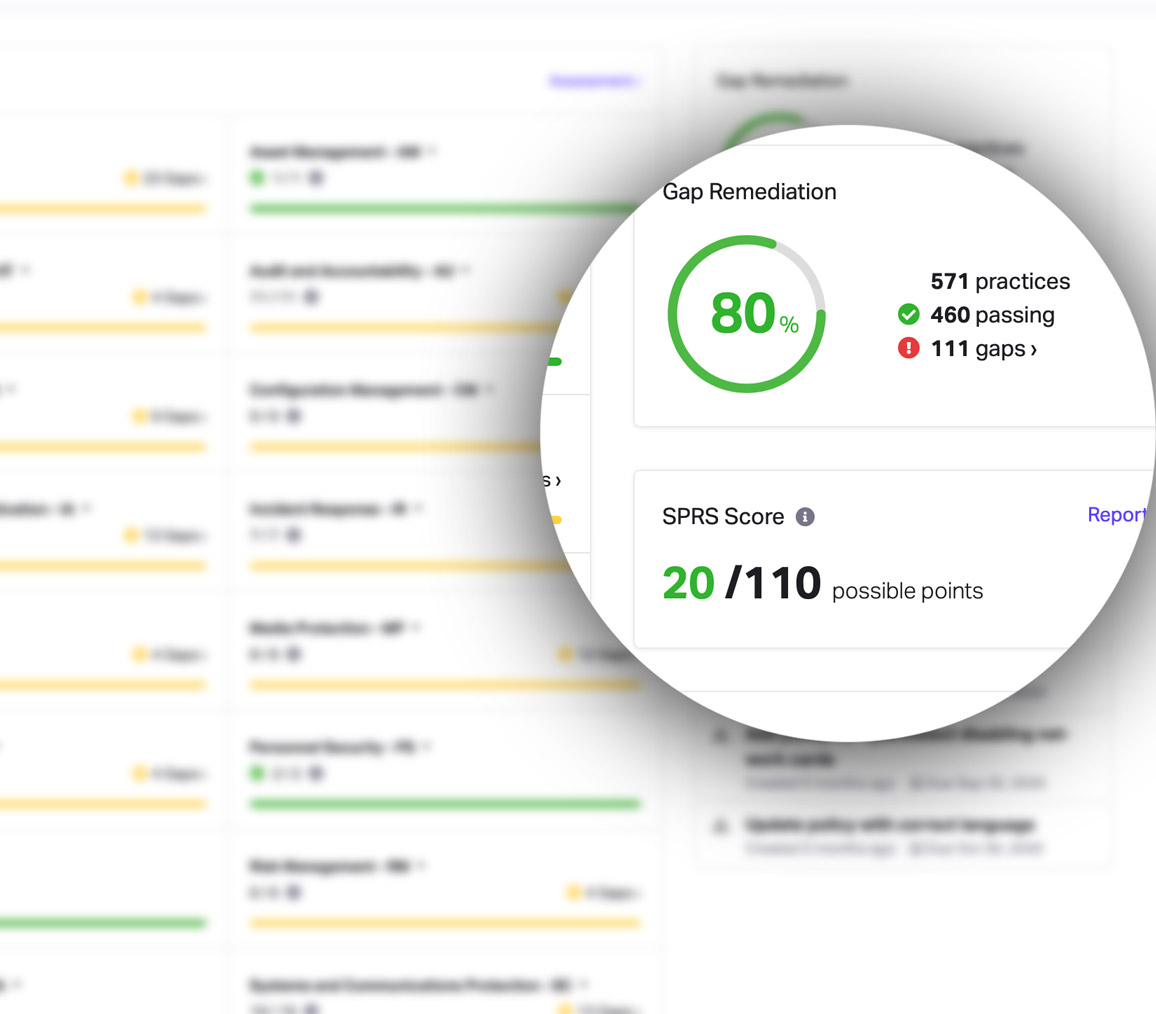
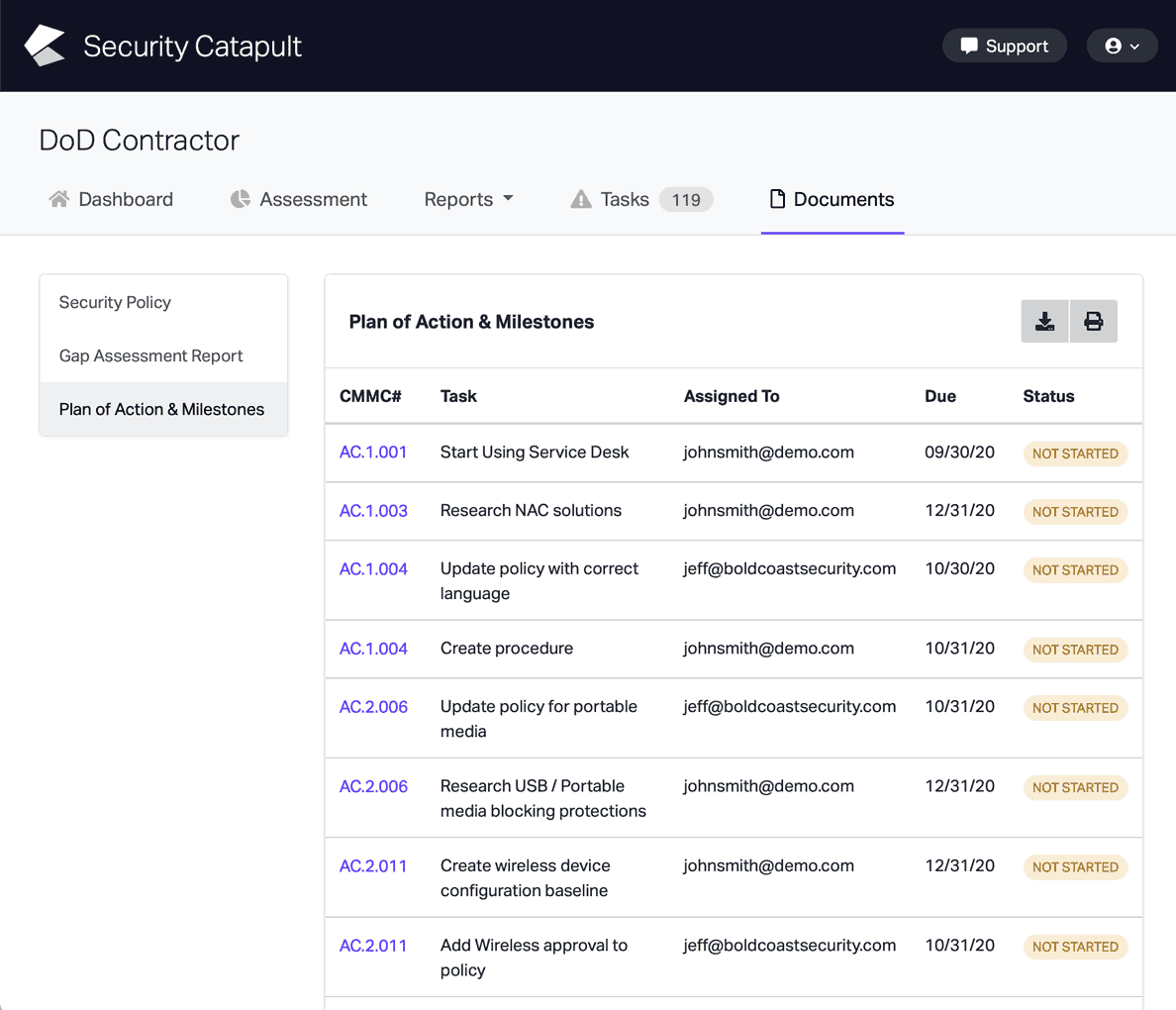
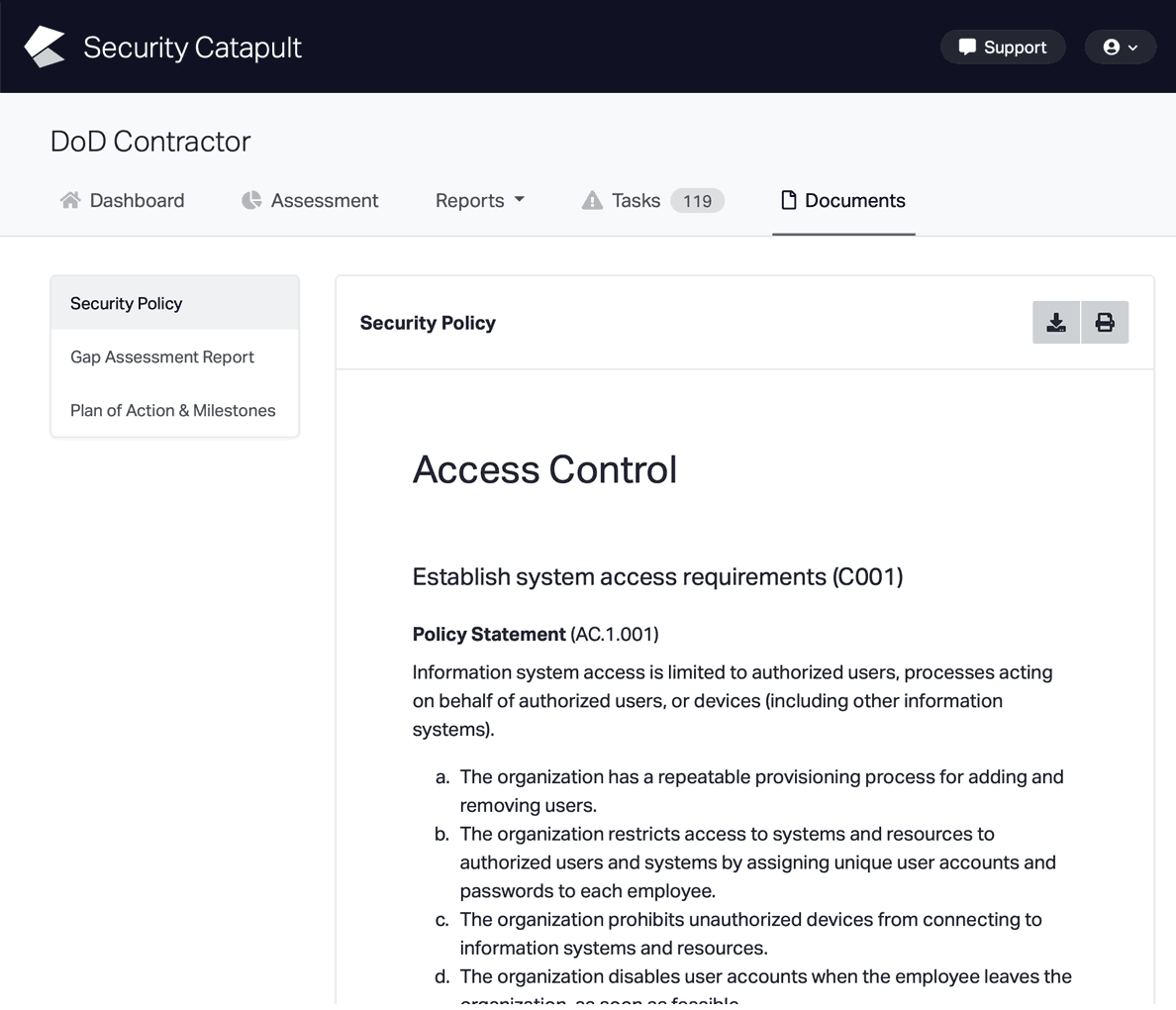
CMMC Practice SC.L1-3.13.5
Public-Access System Separation: Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
Monarch ISC Guidance
Discussion From Source
References
- FAR Clause 52.204-21 b.1.xi
- UK NCSC Cyber Essentials
- NIST SP 800-171 Rev 2 3.13.5
- CIS Controls v7.1 14.1
- NIST CSF v1.1 PR.AC-5
- NIST SP 800-53 Rev 4 SC-7