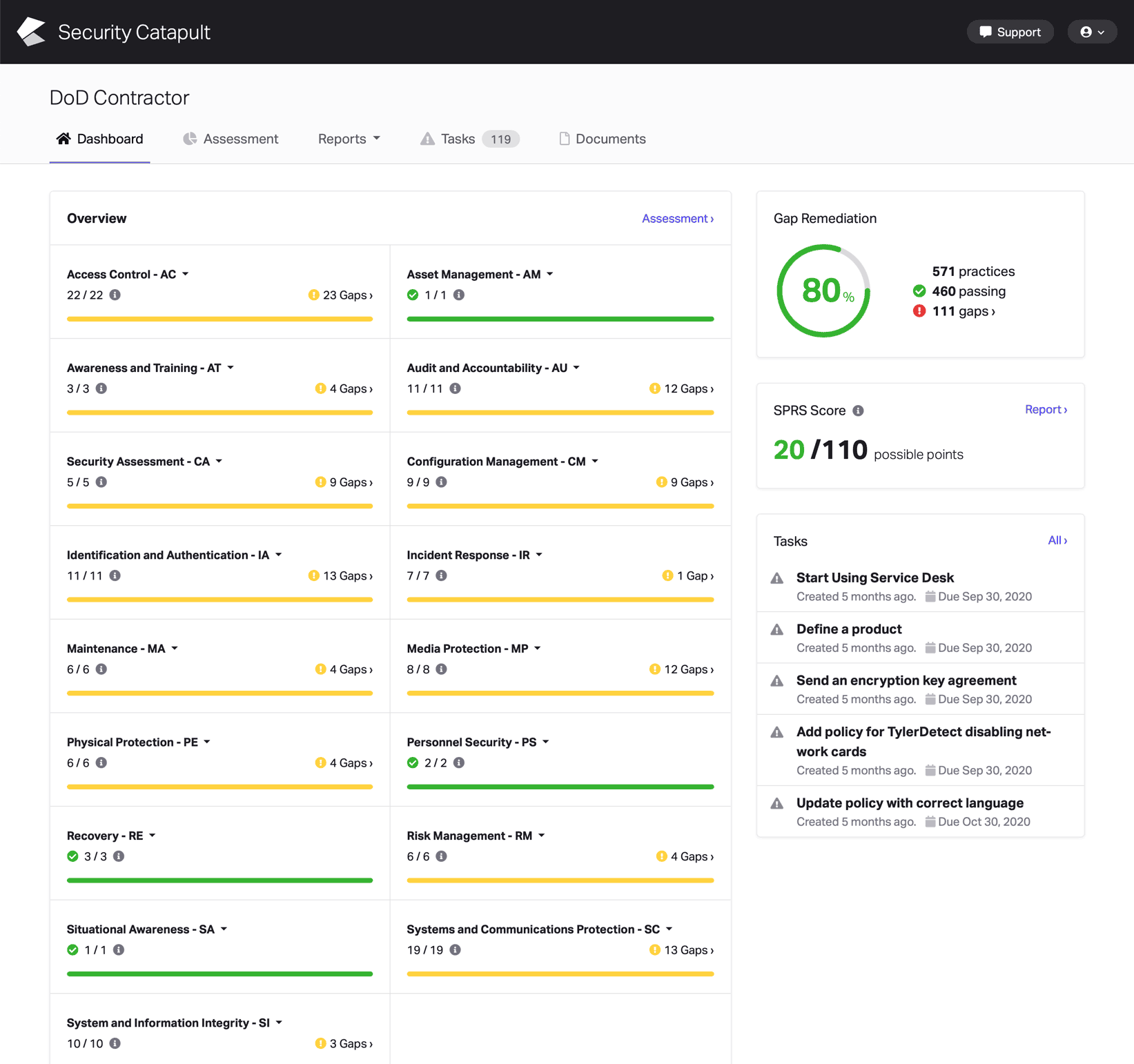
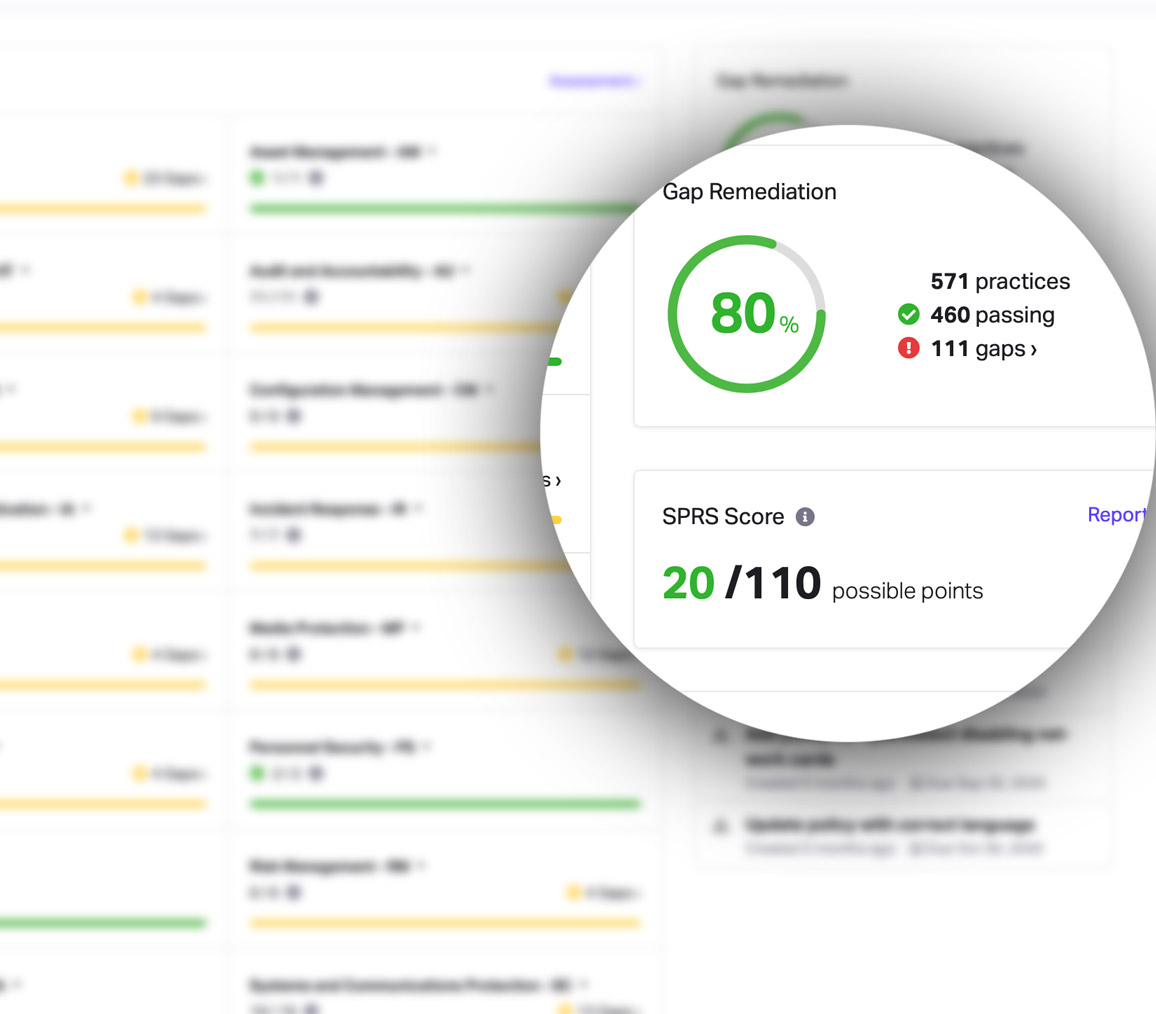
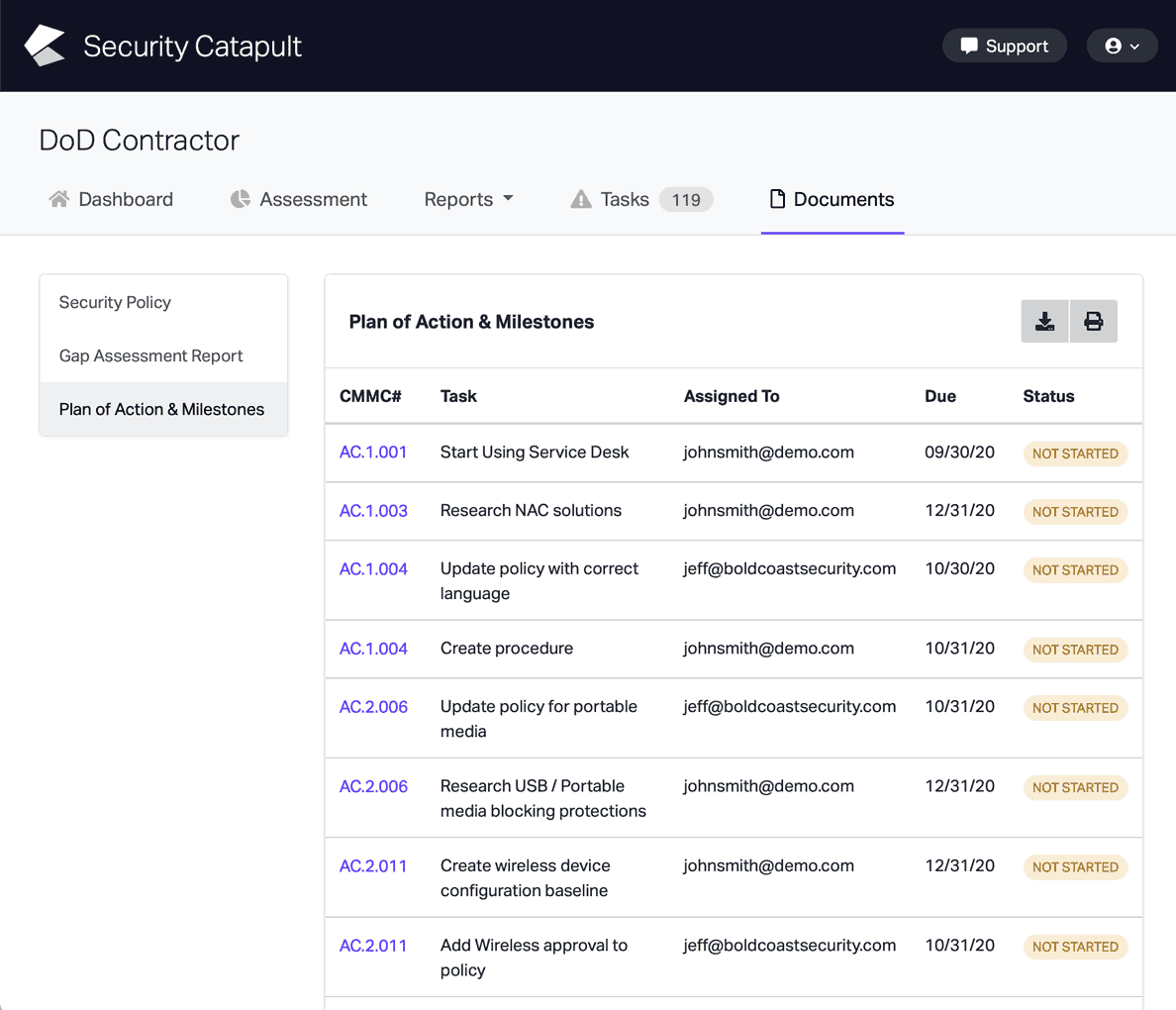
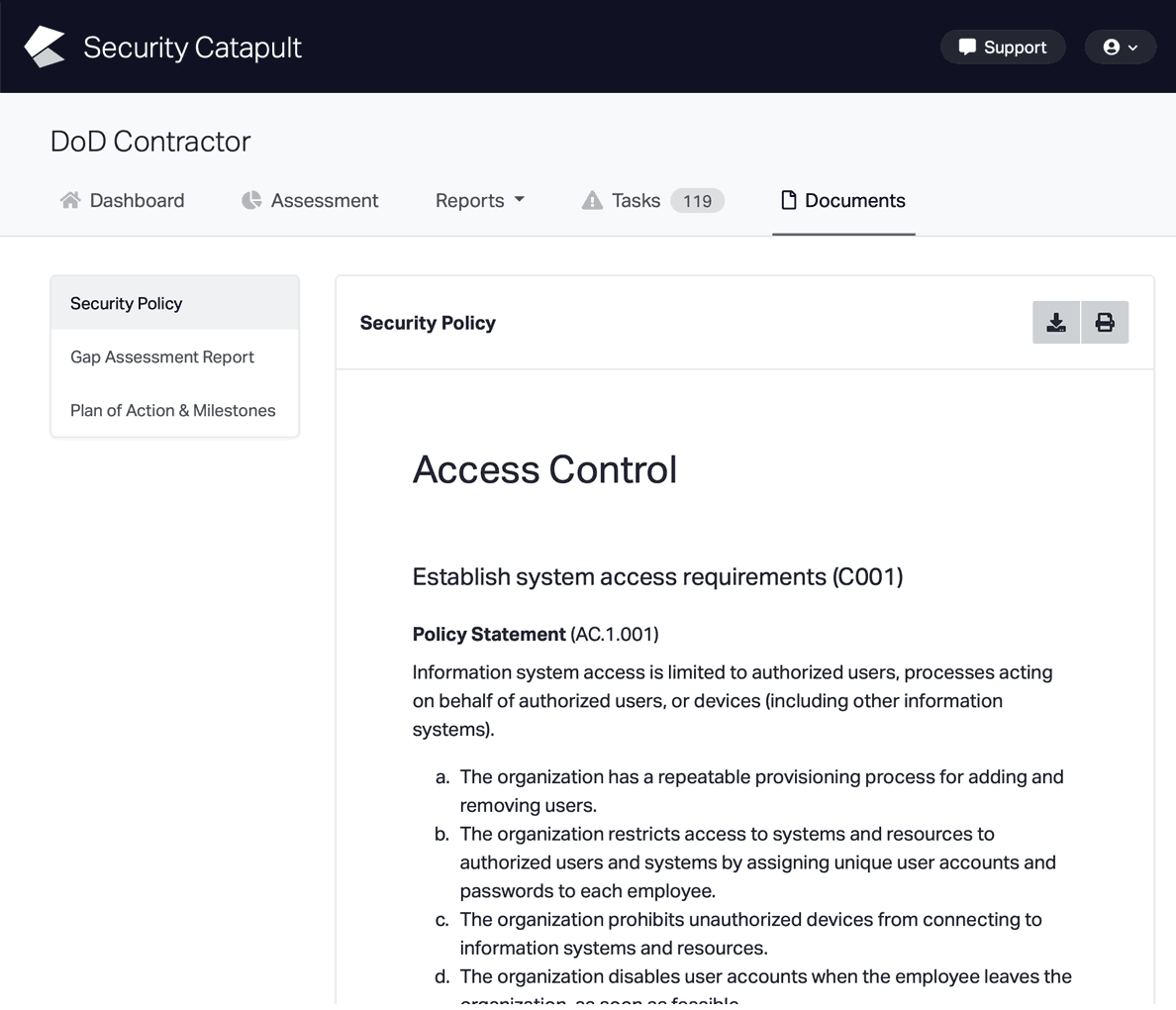
CMMC Practice SC.L2-3.13.3
Role Separation: Separate user functionality from system management functionality.
Monarch ISC Guidance
Discussion From Source
References
- AU ACSC Essential Eight
- NIST SP 800-171 Rev 2 3.13.3
- CIS Controls v7.1 4.3
- CERT RMM v1.2 KIM:SG2.SP2
- NIST SP 800-53 Rev 4 SC-2