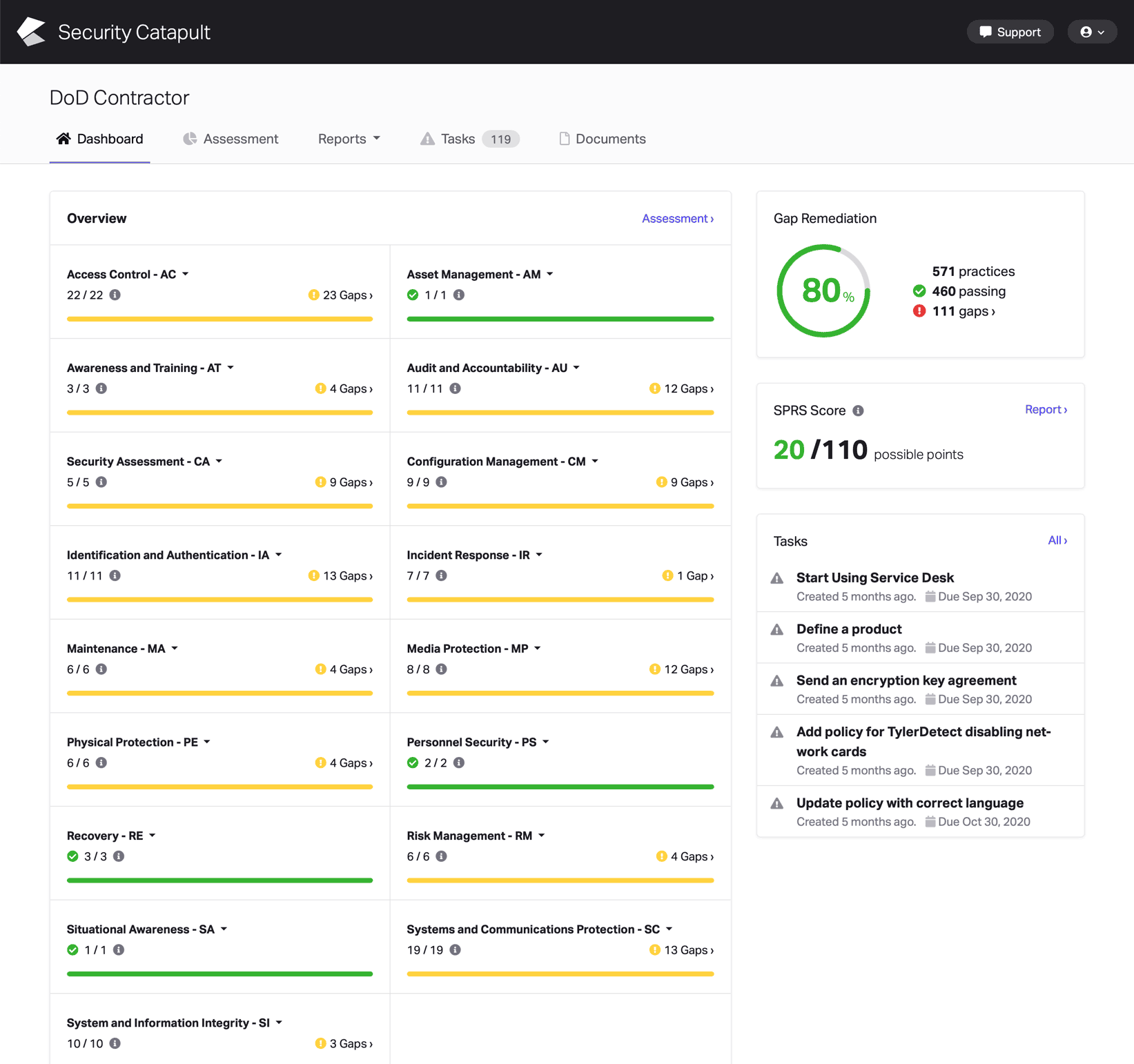
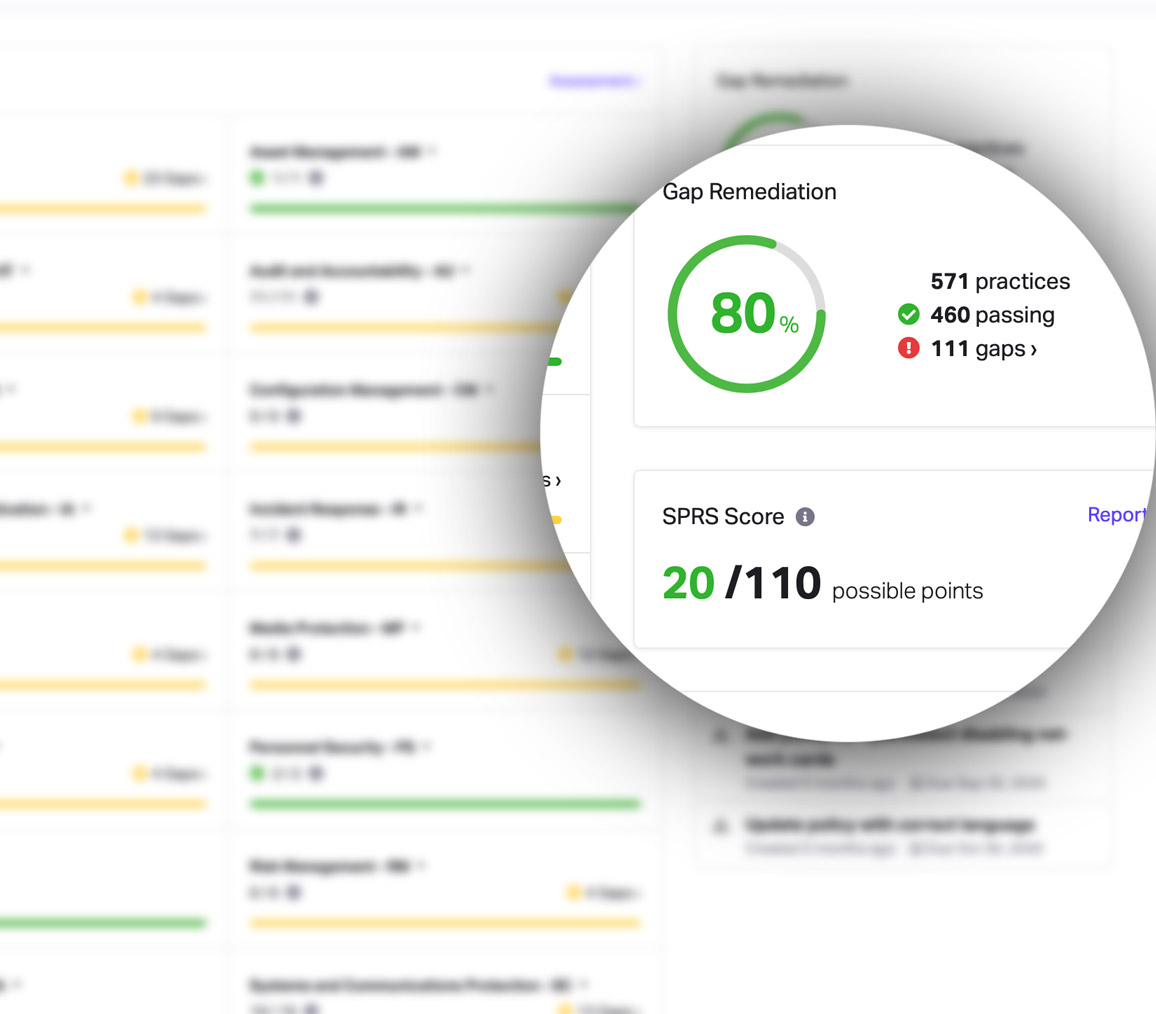
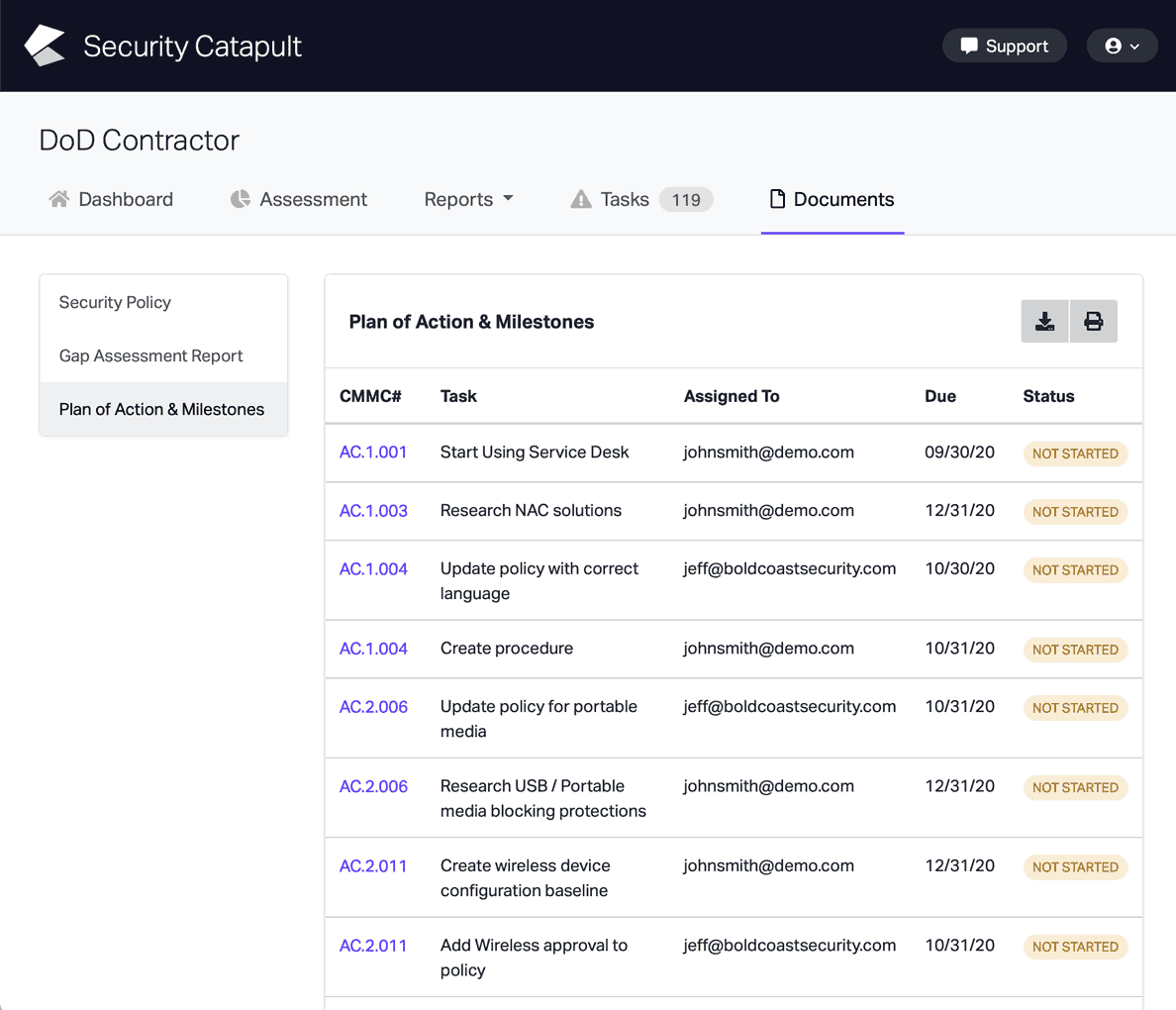
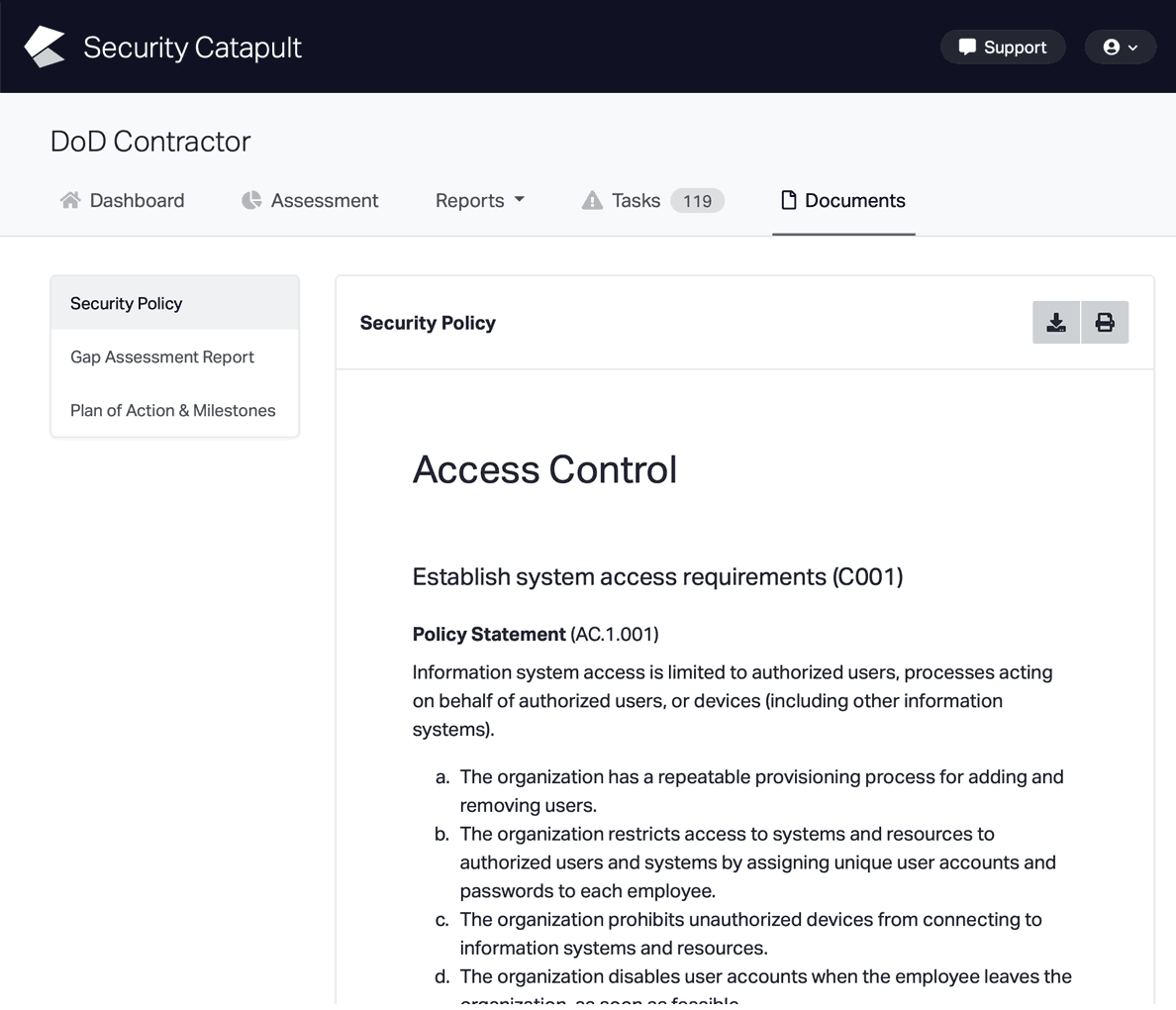
CMMC Practice SI.L1-3.14.1
Flaw Remediation: Identify, report, and correct system flaws in a timely manner.
Monarch ISC Guidance
Discussion From Source
References
- FAR Clause 52.204-21 b.1.xii
- AU ACSC Essential Eight
- UK NCSC Cyber Essentials
- NIST CSF v1.1 RS.CO-2, RS.MI-3
- NIST SP 800-53 Rev 4 SI-2
- NIST SP 800-171 Rev 2 3.14.1
- CERT RMM v1.2 VAR:SG2.SP2